Brilliant Tips About How To Detect Rogue Access Points
![Pdf] A Flexible Framework For Rogue Access Point Detection | Semantic Scholar](https://www.tanaza.com/tanazaclassic/wp-content/uploads/2017/07/RogueAP.png)
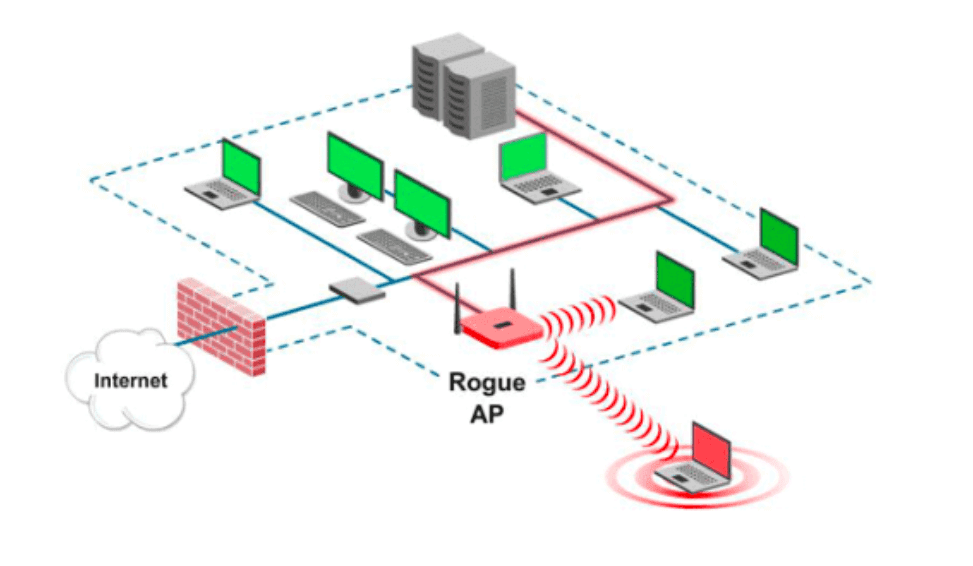
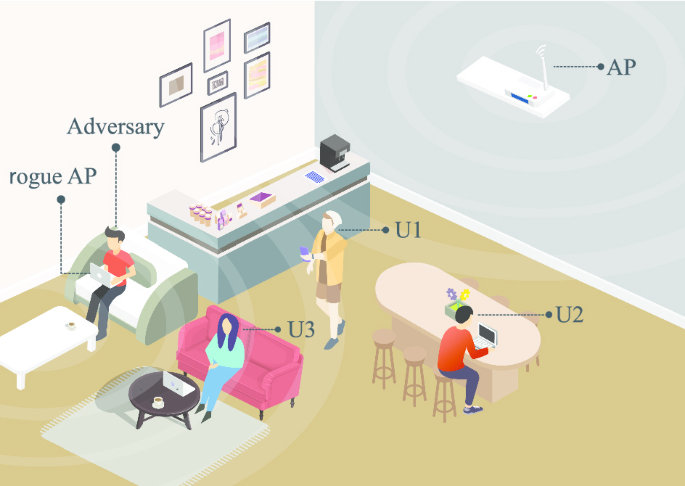
Cisco meraki defines a rogue access point as an ap that is both “seen” on the lan and is broadcasting ssids that are visible to the.
How to detect rogue access points. Those should find both an open and closed port on most waps, which improves os detection accuracy. Rogue aps can be detected by logging into your router as a system administrator. Rogue wireless access points can present some serious problems for your network.
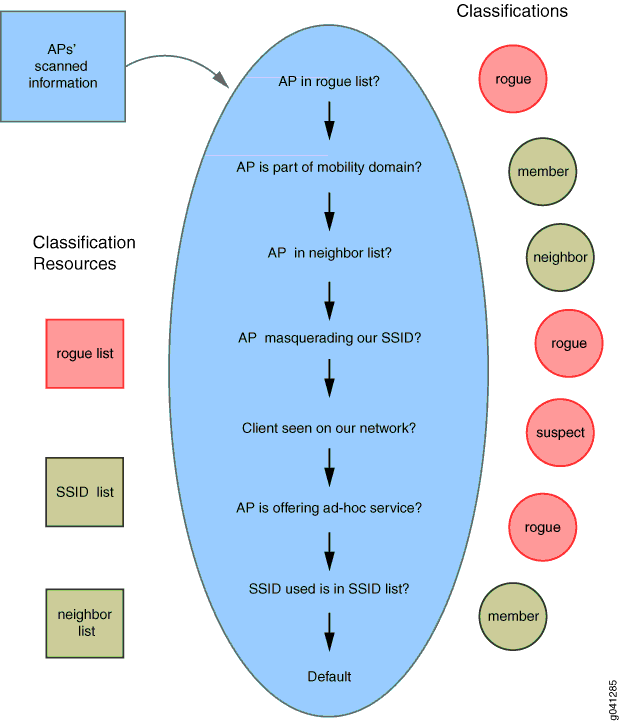
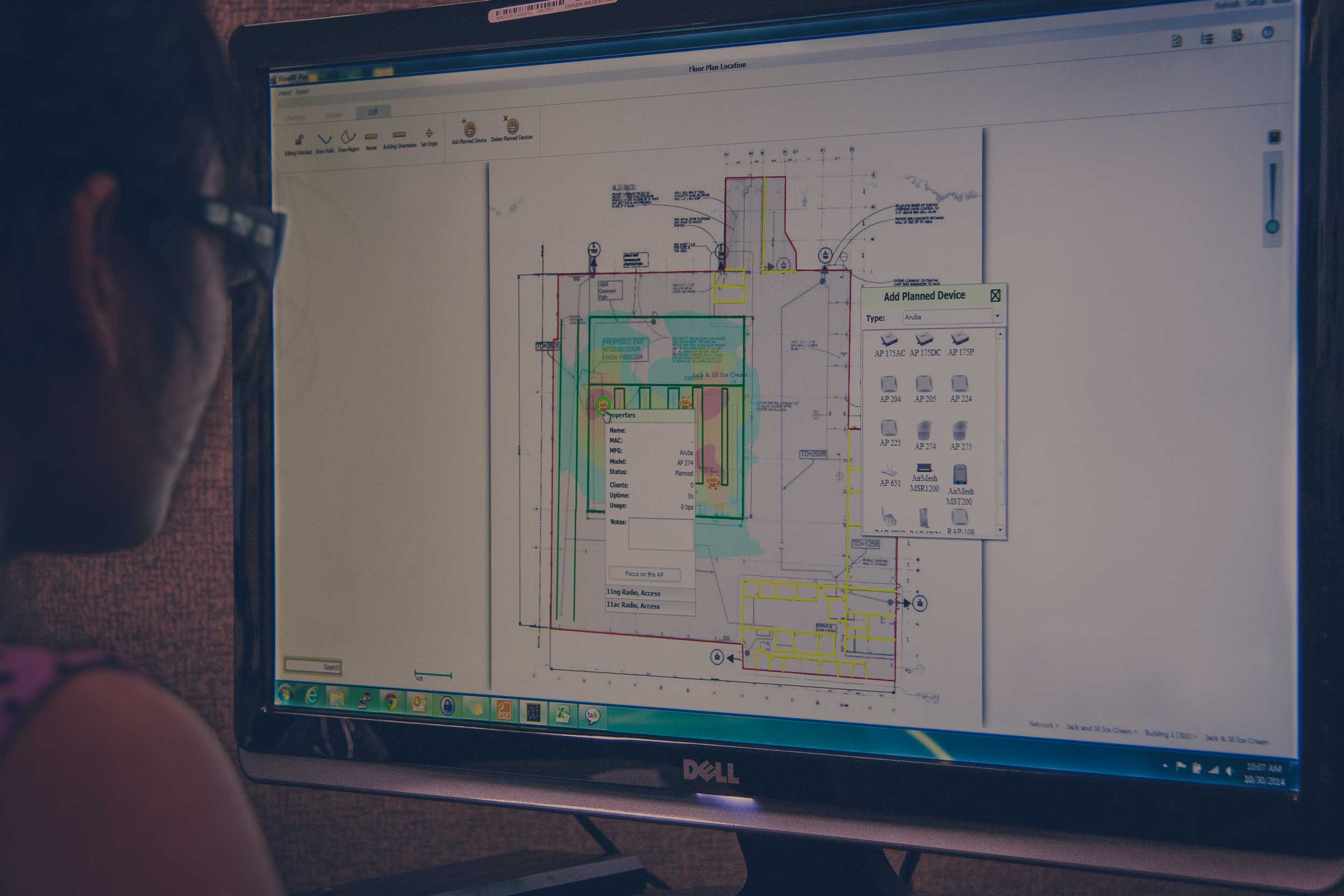
In rogue ap detected table, check the box for the access. What makes a rogue access point rogue? Network performance monitor (npm) as.
First i’ll use ifconfig to identify the alfa wnic: Loginask is here to help you access rogue access point detected quickly and. Click the rogue ap detection on radio button.
There are a couple of ways of detecting rogue aps. Monitor thin and thick aps and their clients. There are two basic approaches for locating rogue access points:
This will show you all of the access points on the network, and if you see something that has not been. In the past, i’ve recommended using netstumbler to identify wireless access points. There it is, ready to get started.
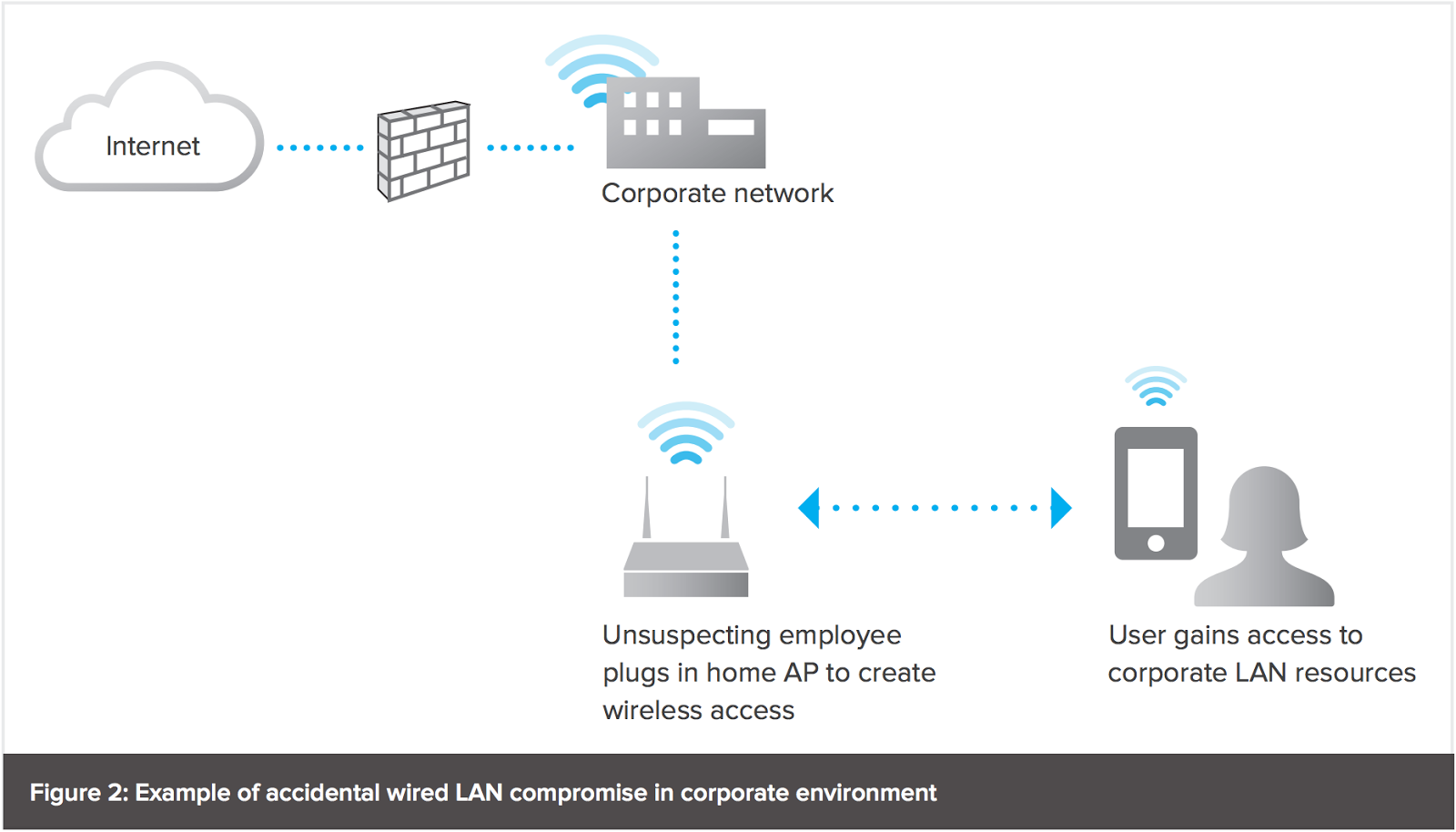
You can configure your wireless firebox to detect rogue wireless access points that operate in the same range as your wireless network. The steps to discover a rogue ap begin with running the port scanner software from a computer connected to the network. This hardware solution uses a system of access points to act as a listening network designed to detect new, rogue access points on the network.
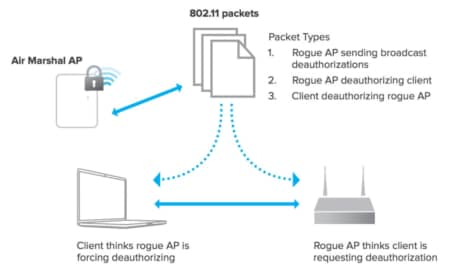
Beaconing, or requesting a beacon, and network sniffing, or looking for packets in the air. A rogue access point is any wireless access point. Rogue access point detected will sometimes glitch and take you a long time to try different solutions.
Using kali linux to find a rogue access point. To authorize detected access points: The first part is just three commands to launch the tool.



![Pdf] A Flexible Framework For Rogue Access Point Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f7a2fec5198aa5b1f3c846b4db50aec4dff4e3b/29-Figure2.2-1.png)